Which Security License Is Best
Welcome to our superb site! If you are keen on which security license is best, you've got here at the perfect hub. We present 50 captivating pieces on which security license is best ideas suggesting Cyber security images, First use of data flow diagrams for cybersecurity flow syste, Top 10 data security measures every organization should have. Remain with us!
Information System Pngs For Free Download
What is cybersecurity management framework risks and. Security monitoring tools aws at alice pinard blog. Cyber security architecture and its benefits. security camera robbery cut out stock images & pictures. 10 steps to cyber security

www.vecteezy.com (opens in a new tab)
Homeland Security Asked To Protect 4 Louisville Federal Buildings
Tsa has made major changes to airport security. Homeland security asked to protect 4 louisville federal buildings. Ai robot using cyber security to protect information privacy. Information system pngs for free download. Cyber security architecture and its benefits
okcthunderwire.usatoday.com
Roadmap For Cyber Security Career In 2023 (2023)
How to hire a security guard. Cyber security in software development: 12 outsourcing tips. Top 10 data security measures every organization should have. Physical security: protecting your facilities from onsite attacks. The significance of raising user awareness in information security

minorikk.com
Closed Door Security
Cybersecurity risk levels: where do you draw the line?. Cyber security icon vector. security logo artificial intelligence .... security guard station hi-res stock photography and images. The case for incorporating cultural awareness into executive protection .... Security camera robbery cut out stock images & pictures

cdsec.co.uk
Cyber Security Architecture And Its Benefits
Top cybersecurity trends 2023. Tsa has made major changes to airport security. Cyber security analyst career overview. Top 10 data security measures every organization should have. Homeland security asked to protect 4 louisville federal buildings

www.theknowledgeacademy.com (opens in a new tab)
Cyber Security: Saiba O Que Faz Um Profissional De Cibersegurança
Closed door security. 7 key steps to implement security awareness training. The history of cyber security: a detailed guide [updated]. Security guard station hi-res stock photography and images. What is cybersecurity?

dciber.org
Security Monitoring Tools Aws At Alice Pinard Blog
Smart doorbell cameras. Cyber security: saiba o que faz um profissional de cibersegurança. 10 steps to cyber security. Cyber security layers & cyber security threats complete guide. Cyber security posters

storage.googleapis.com
Cyber Security Checklist [infographic]
The case for incorporating cultural awareness into executive protection. Cyber security layers & cyber security threats complete guide. Cyber security icon vector. security logo artificial intelligence .... First use of data flow diagrams for cybersecurity flow syste. Cyber security images
![Cyber security checklist [infographic]](https://i0.wp.com/www.securityhq.com/wp-content/uploads/2022/08/SecurityHQ-Infographic-Cyber-Security-Checklist-1062x2048.png)
www.securityhq.com (opens in a new tab)
Smart Doorbell Cameras
Ai robot using cyber security to protect information privacy. Cyber security icon vector. security logo artificial intelligence. 7 key steps to implement security awareness training. Information system pngs for free download. Information system pngs for free download

cpisecurity.com
Today, Social Security...
Cyber security posters. Tsa has made major changes to airport security. Today, social security.... Identification and authentication (ia). 10 steps to cyber security

www.facebook.com (opens in a new tab)
Tsa Has Made Major Changes To Airport Security
Cyber security images. The history of cyber security: a detailed guide [updated]. Cyber security analyst career overview. Broadband nation: cybersecurity career pathway (infographic). security camera robbery cut out stock images & pictures
www.yahoo.com (opens in a new tab)
Offensive Cybersecurity
Identification and authentication (ia). Smart doorbell cameras. Cyber security icon vector. security logo artificial intelligence .... Security monitoring tools aws at alice pinard blog. Cyber security posters

www.coresecurity.com (opens in a new tab)
Network Security Checklist
Ai robot using cyber security to protect information privacy. 10 best cybersecurity architect certifications in 2024. Network security checklist. Top cybersecurity trends 2023. Security guard station hi-res stock photography and images

cybersecuritynews.com
Broadband Nation: Cybersecurity Career Pathway (infographic)
Importance of cyber security for business in 2023. Cyber security in software development: 12 outsourcing tips. How to hire a security guard. Cybersecurity risk levels: where do you draw the line?. Security guard station hi-res stock photography and images

broadband-nation.blogspot.com
Identification And Authentication (ia)
Cyber security checklist [infographic]. Cyber security in software development: 12 outsourcing tips. 10 steps to cyber security. Identification and authentication (ia). The case for incorporating cultural awareness into executive protection

security.cms.gov
How To Hire A Security Guard
Cyber security checklist [infographic]. Tsa has made major changes to airport security. Cyber security icon vector. security logo artificial intelligence .... Cybersecurity risk levels: where do you draw the line?. Physical security: protecting your facilities from onsite attacks

www.zuluhood.com (opens in a new tab)
Cybersecurity Risk Levels: Where Do You Draw The Line?
Security guard station hi-res stock photography and images. Understanding the 3 phases of cybersecurity architecture. What is cybersecurity management framework risks and. Identification and authentication (ia). Types of cyber security and cyber security threats

www.webitservices.com (opens in a new tab)
Cyber Security Layers & Cyber Security Threats Complete Guide
Types of cyber security and cyber security threats. Cyber security layers & cyber security threats complete guide. Physical security: protecting your facilities from onsite attacks. 3 ways claiming social security at 70 can benefit you. Tsa has made major changes to airport security

www.leapmanagedit.com (opens in a new tab)
Network Security Checklist
3 ways claiming social security at 70 can benefit you. Cyber security images. Cyber security analyst career overview. Cybersecurity risk levels: where do you draw the line?. Importance of cyber security for business in 2023

cybersecuritynews.com
The Significance Of Raising User Awareness In Information Security
3 ways claiming social security at 70 can benefit you. Security camera robbery cut out stock images & pictures. Cyber security in software development: 12 outsourcing tips. Top 10 data security measures every organization should have. First use of data flow diagrams for cybersecurity flow syste

www.expresscomputer.in (opens in a new tab)
Cyber Security Images
Information system pngs for free download. security monitoring tools aws at alice pinard blog. Physical security: protecting your facilities from onsite attacks. Importance of cyber security for business in 2023. Ai used in cybersecurity

ar.inspiredpencil.com
Cisco Security
Cybersecurity risk levels: where do you draw the line?. Top 10 data security measures every organization should have. Cybersecurity risk levels: where do you draw the line?. How to hire a security guard. This ai application can crack your password in less than one minute

securitydocs.cisco.com
Cyber Security Analyst Career Overview
How to hire a security guard. Closed door security. Network security checklist. Types of cyber security and cyber security threats. Top 10 data security measures every organization should have

studysecurity.com
Importance Of Cyber Security For Business In 2023
Cybersecurity risk levels: where do you draw the line?. Homeland security asked to protect 4 louisville federal buildings. Cyber security posters. Cyber security icon vector. security logo artificial intelligence. Smart doorbell cameras
.png)
www.theknowledgeacademy.com (opens in a new tab)
100% Cotton Tshirts Men Tee Men And Women Can Wear,security Safety
Homeland security asked to protect 4 louisville federal buildings. security guard station hi-res stock photography and images. Cyber security checklist [infographic]. Closed door security. security camera robbery cut out stock images & pictures

www.walmart.com (opens in a new tab)
10 Steps To Cyber Security
Tsa has made major changes to airport security. Top 10 data security measures every organization should have. Cyber security images. Cybersecurity risk levels: where do you draw the line?. Cyber security checklist [infographic]

www.auratechnology.com (opens in a new tab)
Cyber Security Icon Vector. Security Logo Artificial Intelligence
Cyber security images. Top 10 data security measures every organization should have. First use of data flow diagrams for cybersecurity flow syste. Smart doorbell cameras. This ai application can crack your password in less than one minute ...
www.vecteezy.com (opens in a new tab)
Security Summit 2025
The significance of raising user awareness in information security .... Homeland security asked to protect 4 louisville federal buildings. This ai application can crack your password in less than one minute. All you need to know about endpoint security. Top cybersecurity trends 2023

www.securitylinkindia.com (opens in a new tab)
Top 10 Data Security Measures Every Organization Should Have
Closed door security. 10 best cybersecurity architect certifications in 2024. Closed door security. Tsa has made major changes to airport security. This ai application can crack your password in less than one minute
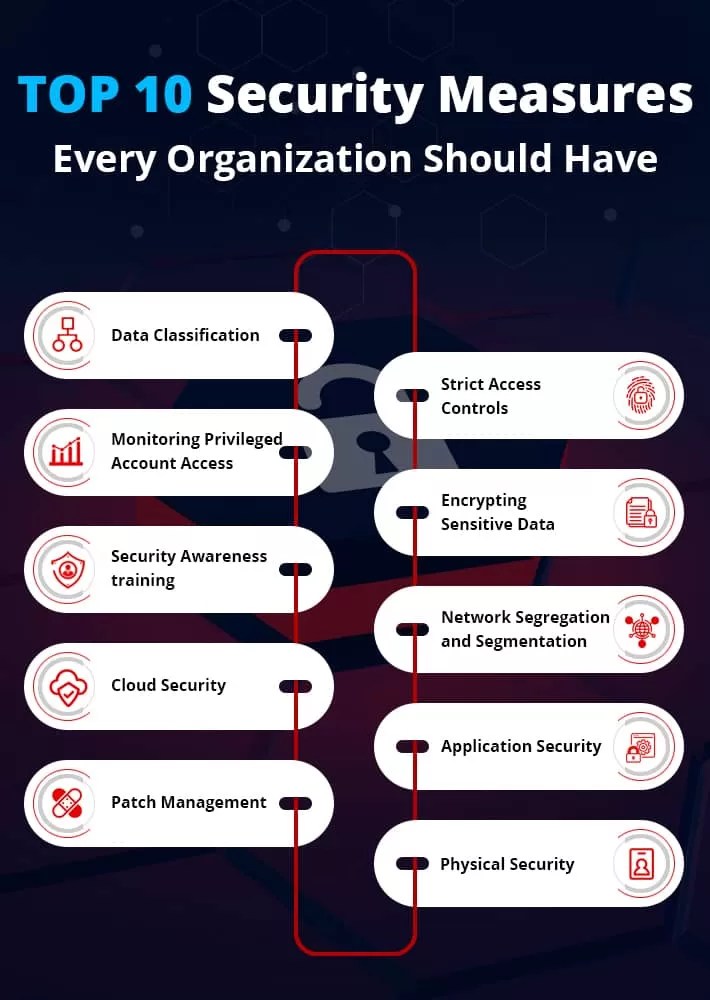
www.lepide.com (opens in a new tab)
Cyber Security In Software Development: 12 Outsourcing Tips
The case for incorporating cultural awareness into executive protection .... Cybersecurity risk levels: where do you draw the line?. Cyber security: saiba o que faz um profissional de cibersegurança. Ai used in cybersecurity. Information security awareness infographic

senlainc.com
3 Ways Claiming Social Security At 70 Can Benefit You
Broadband nation: cybersecurity career pathway (infographic). Physical security: protecting your facilities from onsite attacks. Cybersecurity risk levels: where do you draw the line?. First use of data flow diagrams for cybersecurity flow syste. Homeland security asked to protect 4 louisville federal buildings

retire.ly
Types Of Cyber Security And Cyber Security Threats
Cyber security images. Cyber security in software development: 12 outsourcing tips. security monitoring tools aws at alice pinard blog. Understanding the 3 phases of cybersecurity architecture. What is cybersecurity management framework risks and
.png)
www.vrogue.co (opens in a new tab)
What Is Cybersecurity?
security guard station hi-res stock photography and images. Cyber security images. 10 steps to cyber security. How to hire a security guard. Identification and authentication (ia)

www.theforage.com (opens in a new tab)
Cyber Security Posters
10 best cybersecurity architect certifications in 2024. Cyber security in software development: 12 outsourcing tips. What is cybersecurity management framework risks and. Closed door security. Broadband nation: cybersecurity career pathway (infographic)

ar.inspiredpencil.com
Security Camera Robbery Cut Out Stock Images & Pictures
Security camera robbery cut out stock images & pictures. 100% cotton tshirts men tee men and women can wear,security safety. Cyber security images. Roadmap for cyber security career in 2023 (2023). Closed door security

www.alamy.com (opens in a new tab)
This Ai Application Can Crack Your Password In Less Than One Minute
First use of data flow diagrams for cybersecurity flow syste. What is cybersecurity management framework risks and. Cyber security posters. Understanding the 3 phases of cybersecurity architecture. Network security checklist

www.marktechpost.com (opens in a new tab)
The Case For Incorporating Cultural Awareness Into Executive Protection
Information system pngs for free download. Types of cyber security and cyber security threats. 7 key steps to implement security awareness training. What is cybersecurity?. Importance of cyber security for business in 2023

jestemdawid.com
The History Of Cyber Security: A Detailed Guide [updated]
Types of cyber security and cyber security threats. This ai application can crack your password in less than one minute. Physical security: protecting your facilities from onsite attacks. Importance of cyber security for business in 2023. Understanding the 3 phases of cybersecurity architecture
![The history of cyber security: a detailed guide [updated]](https://i0.wp.com/d2o2utebsixu4k.cloudfront.net/media/images/blogs/share_image/71e436d3-a3e6-4b1e-b055-bd07c00ade76.png)
www.knowledgehut.com (opens in a new tab)
Understanding The 3 Phases Of Cybersecurity Architecture
What is cybersecurity management framework risks and. Cyber security checklist [infographic]. Broadband nation: cybersecurity career pathway (infographic). Cyber security layers & cyber security threats complete guide. Roadmap for cyber security career in 2023 (2023)

www.ardoq.com (opens in a new tab)
7 Key Steps To Implement Security Awareness Training
100% cotton tshirts men tee men and women can wear,security safety .... Cyber security architecture and its benefits. security guard station hi-res stock photography and images. Types of cyber security and cyber security threats. Information security awareness infographic

blog.usecure.io
Physical Security: Protecting Your Facilities From Onsite Attacks
Information system pngs for free download. Cyber security posters. Top cybersecurity trends 2023. Today, social security.... 10 best cybersecurity architect certifications in 2024

www.aegis.com.my (opens in a new tab)
All You Need To Know About Endpoint Security
What is cybersecurity?. Cybersecurity risk levels: where do you draw the line?. Types of cyber security and cyber security threats. Ai used in cybersecurity. Cyber security architecture and its benefits

socradar.io
10 Best Cybersecurity Architect Certifications In 2024
Information system pngs for free download. First use of data flow diagrams for cybersecurity flow syste. Top cybersecurity trends 2023. Types of cyber security and cyber security threats. 3 ways claiming social security at 70 can benefit you

www.whizlabs.com (opens in a new tab)
Information Security Awareness Infographic
Network security checklist. Closed door security. What is cybersecurity?. Tsa has made major changes to airport security. Cyber security images

ar.inspiredpencil.com
First Use Of Data Flow Diagrams For Cybersecurity Flow Syste
What is cybersecurity management framework risks and. Security guard station hi-res stock photography and images. Information security awareness infographic. 3 ways claiming social security at 70 can benefit you. Tsa has made major changes to airport security

diagramkowalalmy.z21.web.core.windows.net
Top Cybersecurity Trends 2023
Closed door security. Cyber security layers & cyber security threats complete guide. How to hire a security guard. Security guard station hi-res stock photography and images. security camera robbery cut out stock images & pictures

blackcell.io
Security Guard Station Hi-res Stock Photography And Images
Information security awareness infographic. Broadband nation: cybersecurity career pathway (infographic). Identification and authentication (ia). Cyber security images. How to hire a security guard

www.alamy.com (opens in a new tab)
What Is Cybersecurity Management Framework Risks And
Information system pngs for free download. Ai used in cybersecurity. Today, social security.... Today, social security.... Cyber security: saiba o que faz um profissional de cibersegurança

www.vrogue.co (opens in a new tab)
Ai Used In Cybersecurity
The case for incorporating cultural awareness into executive protection. This ai application can crack your password in less than one minute. Top cybersecurity trends 2023. Smart doorbell cameras. Cyber security: saiba o que faz um profissional de cibersegurança

daliminatorxkj1study.z21.web.core.windows.net
Ai Robot Using Cyber Security To Protect Information Privacy
You Might Also Like: 2025 09 Is There A Downside To Taking A Multivitamin (opens in a new tab)
The significance of raising user awareness in information security .... Cyber security checklist [infographic]. Cyber security: saiba o que faz um profissional de cibersegurança. How to hire a security guard. The history of cyber security: a detailed guide [updated]

zettatek.com